Comm100 Agent SSO allows your agents to have a single login across Comm100 and other applications. You only need to log in once and can move swiftly between Comm100 and other applications without the need to log into separate accounts or remember multiple usernames and passwords.
Comm100 supports Agent SSO via SAML (Security Assertion Markup Language) or JWT (JSON Web Token). This article introduces the steps on how you can enable SSO using JWT. If a user is authenticated by an identity provider via JWT, they can securely access the Comm100 account without providing separate login credentials.
As Comm100 account admin, please read the following sections to enable the JWT Agent SSO option in your Comm100.
- Required Information for Enabling JWT SSO
- Enable JWT SSO in your Comm100 Account
- User Management after Enabling JWT SSO
- Log into your Comm100 Account with SSO
Required Information for Enabling JWT SSO
JWT SSO provides a security mechanism that allows your Comm100 account to trust the sign-in request obtained from your systems. Therefore, if you want to set up JWT SSO, please meet with your tech team responsible for your JWT authentication system to ensure that your company has a JWT service accessible by Comm100 users.
Please ask your tech team to provide the following information:
- The remote login URL for your JWT service that Comm100 will redirect your agents to for remote authentication.
- (Optional)The remote logout URL where comm100 can redirect users after they sign out of Comm100.
To configure the JWT authentication system, your tech team, usually your IT Department, may require some additional information from Comm100. Please ask your team to refer to the Technical Implementation Details at the end of this article.
After you get all the required information ready, read the following section to learn how to Enable JWT SSO in your Comm100 Account.
Enable JWT SSO in your Comm100 Account
- Log in to your Comm100 Control Panel and navigate to the Global Settings module.
- Click Security on the left, and enable Agent Single Sign-On.
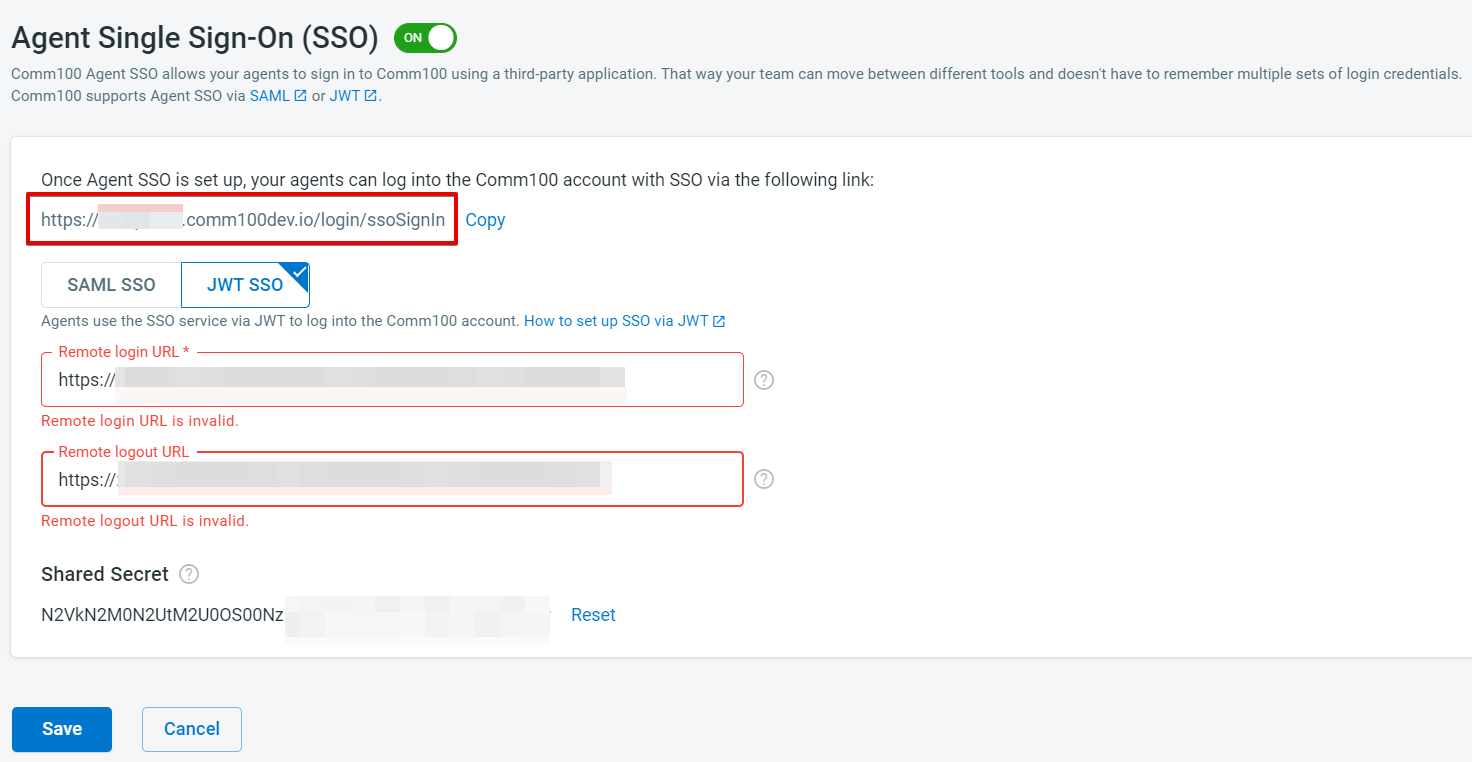
- Switch to JWT SSO, and fill in the required information.
As we mentioned in the first section of this article, please collaborate with your tech team and get the mentioned Remote Login URL and Remote Logout URL. The Shared Secret is randomly generated the moment you enable JWT SSO. This is a shared secret token between you and Comm100. Submit it to your tech team as they will need it for JWT authentication.
You can also find the SSO login URL displayed on the page, share this link with your agents as they will need it to log into Comm100 once you set up Agent SSO. - Click to Save Changes.
User Management after Enabling JWT SSO
After you enable Agent SSO, note that:
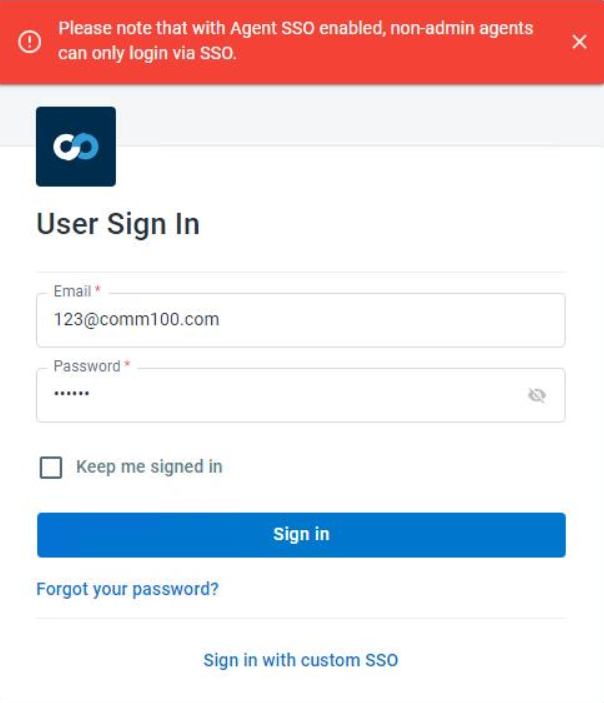
- Only your account admin can use their Comm100 email and password to log into their Comm100 account once Agent SSO with SAML or JWT authentication has been enabled. Non-admin agents can be only signed into Comm100 via the enabled SSO platform. When trying to log in using Comm100 credentials, non-admin agents will receive an error message.
- After Agent SSO is enabled, non-admin agents' Comm100 passwords cannot be reset, whether by themselves or by the account admin.
- Only after your account admin creates an agent account with an email address that matches one in your SSO platform, can an agent sign into their Comm100 account via JWT SSO.
Log into your Comm100 Account with SSO
After you enable agent SSO and connect Comm100 to your SSO platform, your non-admin agents will need to log into Comm100 via your SSO service.
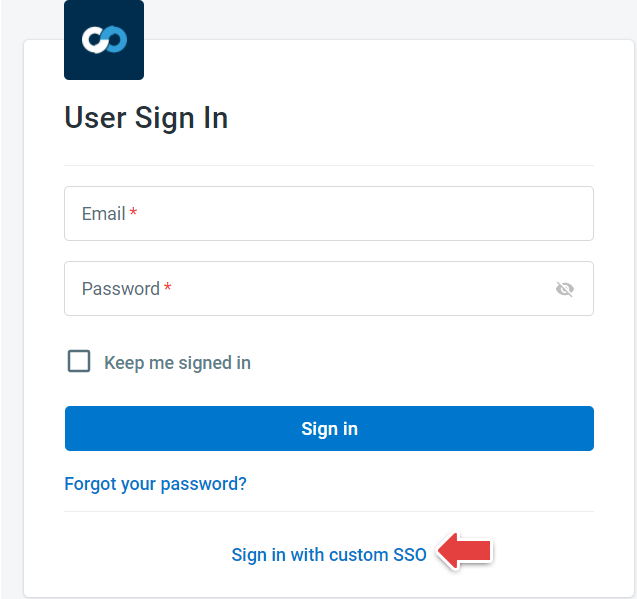
- Go to your account User Sign-In page.
- Click Sign in with Custom SSO.
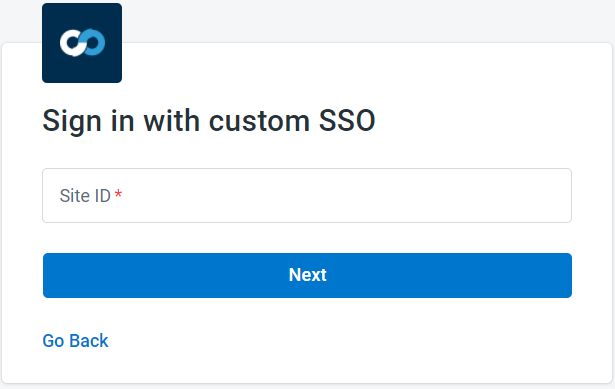
- Provide your Comm100 Site ID and click Next.
Note: If you are not sure about your Comm100 site ID, please consult your Comm100 account admin or refer to this article How to Find My Site ID.
As mentioned in the previous section, in your JWTSSO configuration page of the Comm100 control panel, you can find the complete SSO login URL which includes the Comm100 Site ID. Example:
https://dash12.comm100.io/login/sso/?siteid=20100000 - Comm100 redirects you to the configured login system according to your JWT implementation.
- If you’ve already signed in to your own login system, you will be authenticated and log into your Comm100 account automatically. If you are not signed in, log into your system first and you will be authenticated and given access Comm100.
Technical Implementation Details
Please ask the relevant tech team in your company who is responsible for the JWT implementation to refer to the following technical details:
- JWT Algorithm and Token Types
- JWT Attributes
- Comm100 JWT SSO endpoint
- Remote Login URL Parameter (redirect_url)
- Code examples for JWT SSO Implementation
JWT Algorithm and Token Type
Please specify HS256 as the JWT algorithm in the header of your JWT payload. HS256 indicates that this token is signed in using HMAC-SHA256.
{
"typ":"JWT",
"alg":"HS256"
}
JWT Attributes
An email address is required for Comm100 to uniquely identify the user. Using the attributes listed in the table below, you can send additional user profile data which will be synced between your user login system and Comm100.
Attribute | Required | Description |
Yes | Email of the user being signed in. It is used to identify the user record in Comm100. | |
name | No | The name of a user. The user in Comm100 will be created or updated accordingly. |
Comm100 JWT SSO endpoint
After successfully authenticating the user, redirect the user along with the JWT payload to the Comm100 endpoint: https://
The payload should be base64-encoded and appended to the URL as a query string. The JWT payload must be sent to your Comm100 system using the https protocol. Here is an example:
https://
Remote Login URL Parameter (redirect_url)
When Comm100 redirects a user to your remote login page, it also passes a URL parameter named redirect_url. The parameter contains the page that Comm100 will return the agent to after your login system has authenticated the agent. Append the parameter (name and value) to the Comm100 JWT endpoint.
Code examples for JWT SSO Implementation
Actually, it is easy for your tech team to implement the JWT SSO. We are also providing JWT SSO examples in our GitHub repository helping you have a quick start with our JWT SSO implementation.